Introduction
In the modern world of technology, having in-depth knowledge of how networking works has become a requirement. If you are involved in server management, then you definitely need to be aware of how it works. Having detailed knowledge about the inner operations of your service will help you keep your services in line. It will help you employ the best solutions and maintain the smooth running of your connections.
The goal of this guide is to equip you with the essential knowledge you need to navigate the world of networking. This includes the most commonly used terminology, as well as the fundamental concepts employed in networking. Knowing about its various components will help you prevent and identify problems as soon as possible. That way, you can deal with them quickly and ensure minimum downtime.
Whether you are currently managing a server or will be in the future, use this tutorial as a guiding principle. Learn the components and the characteristics before you dive into the functionalities of your server. Here you will find the nitty-gritty of networking and server management. Let’s get started!
The Most Common Networking Terms
Before you dive into the layers and components, you need to figure out the language you will be using in this environment. There are many terms that will sound familiar in this list. These are used by any of us on a day-to-day basis but most of us do not actually know what they mean. We will help you understand these basic terms in the context of servers and networking. This will make a lot of your processes easier to follow and understand. We will continue to use these terms and further explain them as we move along the guide.
- Connection
A network is a web of components that are linked by various connections. But what does it mean in the context of networking?
A connection in networking constitutes data or information that is traveling through the network. You actually need to establish a connection before you transfer data between two points in the network. The protocol of the environment determines how you establish this connection. When you are done with the data transfer, you can close the connection.
- Packet
Welcome to the fundamental units of a network: packets. Imagine if your data was tangible material; you would have to organize it in various packets in order to be able to ship it to another location safely. Similarly, even in a digital network, your data has to be put in packets before the transfer. This divides your data into discrete pieces to make communication easier within the network.
A data packet typically consists of two main parts. You have the header portion and the main portion. The header portion precedes the main body of the packet. It contains information about the packet and its specifics. For example, it may contain the source of the packet, its destination, the timestamps it has, its network hops, and several other specifics.
The main part of the packet constitutes, as expected, the actual data. Also called the body or the payload, this is the information that you want to transfer to another point in the network.
- Interface
When you think of an interface, you think of something akin to a dashboard. It is the platform that you can interact with to control the rest of the operations. In such a setting, your interface may be virtual or physical. A virtual or digital interface is accessed through a software. A physical interface will be associated with a physical device or some hardware. You can modify, alter, and control your network using the specific interface associated with it.
- LAN
Most of us have probably heard the terms LAN and WAN thrown around quite often. But did you know that LAN stands for Local Area Network? You can understand the way it works by what it is called. A Local Area Network restricts your data to the local circle only. This means that the data on your LAN is not accessible to the rest of the internet. It remains within the boundaries you have set, such as your home or office network.
- WAN
On the other hand, WAN stands for Wide Area Network. As you can probably already tell, this network covers a greater width. These networks are typically large, spanning over large distances, often referring to the entire internet. Hence, if your interface is connected to WAN, you can access it using the internet.
- Protocol
Think of the protocol as the instruction manual of the rulebook. It defines all the rules and standards that all the components in the given network have to adhere to. It contains the language that the system uses to communicate within itself. There are many different types of protocols that are used in networking, such as UDP, IP, and HTTP. Some are low level while others are application layers. We will explore the world of networking protocols in detail later on in this guide.
- Port
The port on a machine is an address. This port is usually connected to a part of the software. The goal of a port is to enable communication between your server and multiple kinds of applications.
- Firewall
If you have ever used a computer, you have most likely heard about or seen a pop-up for a firewall. A firewall is a program that gives your system security. It does so by limiting and monitoring the traffic that goes in and out of your system. When talking about firewalls for servers, it is a program that decides which traffic should be able to go in and come out of your server. To do this, it allows you to configure certain rules. Using these rules, you can determine which port should be able to send and receive traffic from your server. You can also block certain ports to prevent communication between it and your server.
You can take a look at our tutorials to get you started on configuring and using firewalls:
- The Basics of UFW: Learning the Essential Firewall Commands
- Setting Up a Firewall with FirewallD on CentOS 7
- Listing and Deleting Iptables Firewall Rules
- NAT
NAT stands for Network Address Translation. You will find NAT in physical LANs where they are used to direct requests from particular IP addresses to the relevant servers. It keeps tabs on the backend servers in the LAN and translates incoming requests to perform accurate routing.
- VPN
VPN stands for Virtual Private Network. A VPN is a digital tool that you can use for security and privacy. It masks your IP address and secures your data packets from hackers and prying eyes. This way, you can safely connect separate LANs and remote systems through the internet.
Get started with setting up VPN connections with our tutorials:
- A How-to Guide: Connect VPN Network to CloudSigma Infrastructure
- Run your own VPN server under Docker with OpenVPN Access Server
- Setting up OpenVPN on Ubuntu 18.04
These were some of the most basic and commonly used terminologies in the world of networking. Of course, we are unable to cover everything on this list. But you will continue to learn as we delve into the network layers and protocols. Use these terms as the basis on which to build your subsequent knowledge of networking systems.
The Various Network Layers
Now that we know what some of the terms mean, we can move onto the organization of a network. The connections in a given network can be seen as a horizontal hierarchy. Each layer comprises technology and protocols that abstract the raw data to make communication simpler for the user and the application. The goal is to reduce the time and effort you need to develop new protocols to handle different types of traffic.
There are different models when it comes to layers in networking, as you will see below. However, regardless of the model, the data path is the same. The data begins at the top of the pathway as you send it out from your machine. It passes through the various layers. At the end of the stand, it transfers to another machine. In the other machine, it will travel up through all the layers. Each layer envelopes the data it gets from the layer before itself to assist the next one in line in dealing with the data.
Here, we will discuss two types of models for the networking layers: the OSI model and the TCP/IP model:
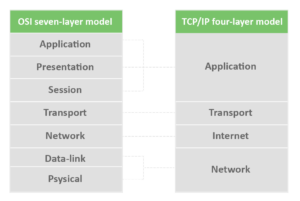
OSI Model and TCP/IP Model
OSI Model
The OSI model stands for Open Systems Interconnect. There are seven different layers that make up this model:
- Application
This is the outermost layers that the user, or yourself, will interact with the most. Through the application layer, you will be able to monitor as well as configure. It will give you information about network communication, resource availability, and data synchronization.
- Presentation
This layer takes care of multiple things, including resource mapping, data translation, and context creation. The presentation layer takes the data from the lower levels and converts it into a form that the application layer can comprehend.
- Session
The sessions layer is responsible for the connection in the network. You can use this layer to create new connections, destroy the ones you do not need, or simply maintain the current connections.
- Transport
The job of the transport layer is to provide the layers after itself reliable connections. It ensures the reliability of the connection by verifying the integrity of the data it is receiving and sending. This means that it can check whether or not the data it sent to the subsequent layers reached in one piece without any loss or damage. In case some data dropped in the middle of the transfer, this layer has the capability to resend it.
- Network
The network layer works to provide routing to the data. It corresponds between the various nodes that constitute the network and tells the data where to go by using addresses for the computers. Not only that, but the network layer divides the data into smaller messages for easy transfer between nodes. The messages are compiled and accurately assembled when they reach the destination.
- Data Link
The data link layer is responsible for maintaining a persistent and reliable link between the nodes in the network. It works with physical connections to establish and retain the links between the devices.
- Physical
Finally, the physical layer works with the physical, tangible devices between which the connections exist. This layer includes the hardware as well as the software it is using.
TCP/IP Model
The second model is the TCP/IP model. Also known as the IP or the Internet Protocol suite, this is a very popular networking model. This is because it is a comparatively more abstract and flexible layering model. Its fluidity makes it easier to implement.
It has four layers only as opposed to the seven layers of the OSI model. As you will see below, many of these layers are similar to some of the ones seen in the OSI layering method.
- Application
Here, the job of the application layer is to create data as well as transfer it. The individual applications are present on remote servers. Each of the applications seems to be operating locally for the user. The application layer creates the user data and then transmits it between the various applications.
- Transport
The transport layer serves to mediate communication within the system. Again, this is where the ports become relevant. The transport layer uses the ports to establish unreliable and reliable connections between the different services on the network. The type of connection you establish depends on the type of protocol you use.
- Internet
This is where the IP model differs from the OSI layering model. The internet layer in this method is responsible for data transmission between the nodes. It does not concern itself with the connection. Rather, it simply uses the knowledge about the connection endpoints to transfer the data. It identifies the source and the destination through IP addresses.
- Link
Lastly, the link layer is what gives the remote systems their identity. It establishes the addressability of the local network and the nodes that constitute it. This is what subsequently enables the internet layer to transmit data.
Network Interfaces
After learning the terminology and the basics of networking layers, you can move on to the interfaces. As we all understand, interfaces are basically communication points. Most servers have one interface for each Ethernet or wireless internet card. You can configure the interface based on your preferences and requirements. Each interface in your network will have a corresponding networking device. This device can be virtual or physical.
One of the virtual network interfaces that the server sets up is the loopback or the localhost interface. Most of your tools will refer to this as the ‘lo’ interface. The job of this interface is to connect the applications and processes on various computers.
Another interface that you will have in your system is to service traffic to the internet. This is usually set up by the administrator. You may also need an interface for a LAN or a private network.
Protocols for Data Transmission
The last thing you need to complete your fundamental education about networking is protocols. Protocols are what define the operations within a system and make a network work. The protocols layer on top of each other and the data is transmitted through all of them.
Next, we will discuss some of the most common protocols that you may use or hear about. The goal is to understand what differentiates them and why they are important for certain processes.
- Media Access Control
To start off, we will begin with a communications protocol which operates in the link layer. The media access control protocol helps us differentiate between various devices through an address. The Media Access Control or MAC address designates the identity of a given device.
Each device gets its MAC address as it is manufactured and it is completely unique. As a result, the network can distinguish every device on the internet using the MAC address. This means that even if the software changes the name of the device, the network will still identify the hardware.
- IP
The IP protocol is one of the most popular protocols in networking. This is because it is one of the protocols that run the internet. We all know that our digital devices have unique “IP addresses”. Belonging to the internet layer in the IP/TCP model, the IP protocol has several different implementations. Most commonly, we see IPv4 and IPv6. The latter is a more improved version of IPv4.
The way the IP protocol works is that it creates multiple pathways to establish a connection with a singular destination. This is because it assumes an unreliable network when the traffic is crossing networks. The protocol can switch between the paths dynamically.
- ICMP
ICMP stands for internet control message protocol. This is a protocol that is particularly useful for network diagnostic tools like ping and traceroute. The ICMP can indicate errors and availability by sending messages between devices. The protocol transmits packets when other data packets in the network encounter some issue in their path. The ICMP detects the error in the transmission.
- TCP
TCP stands for transmission control protocol. Belonging to the transport layer of the IP/TCP layering model, TCP is involved in data packaging and transmission. It is one of the most critical protocols that govern our internet.
Before it deals with the data transfer, the protocol has to establish a connection. To do this, TCP uses a three-way handshake. Here, two endpoints in the communication line have to accept the request and ensure a reliable connection for data transmission.
It performs a variety of functions in the network. To begin with, it envelopes data into packets and transfers them through the relevant connections. Secondly, TCP checks for errors in the system. Not only that, but it is also capable of assembling data packets for the application layer. Once the data reaches the destination, TCP destroys it using a four-way handshake.
- UDP
UDP stands for user datagram protocol. Many people often use it in combination with TCP since it is used in the transport layer as well. What differentiates it from the latter is that it establishes an unreliable connection. An unreliable data transfer means that the protocol does not verify whether or not the date has safely been received on the other end of the connection.
You may be thinking why would anyone use unreliable connections over reliable connections anyway? There are, however, many useful applications of unreliable data transfer like what UDP provides. For example, people implement UDP in applications where time is of the essence. Instead of waiting for confirmation that the data has been received, the system simply launches the data from its end. That is why you will find its use in things like games and VOIP.
- HTTP
HTTP stands for hypertext transfer protocol. You should be familiar with this protocol considering all websites begin with these four letters. Implemented in the application layer, HTTP defines functions that help your system acknowledge what the user is requesting.
For example, some of the functions include GET, POST, and DELETE. Each of these interacts with the data differently, performing the action suggested by the name. As such, HTTP accounts for the communication of your system with or on the internet.
- FTP
FTP stands for file transfer protocol. Also implemented in the application layer, this protocol is responsible for transferring files between hosts. Although it is important to remember that this is not a secure protocol. That is why it is mostly used in public settings.
- DNS
DNS stands for domain name system. Another application layer protocol that allows you to easily name your internet resources. The names are human-friendly and connect the domain to the IP address so you can access it with ease.
- SSH
SSH is an application layer protocol that stands for secure shell. As suggested by its name, it is an end-to-end encrypted protocol. You can use it to make combinations with the remote server safer. It is a ubiquitous protocol, therefore many additional technologies are built around it.
In addition, here are in-depth tutorials on implementing the SSH protocol:
- Configuring Your Linux Server to Use SSH Key-Based Authentication
- How To Use SSH to Connect to a Remote Server in Ubuntu
- Automatically Inject SSH Keys into your Cloud Servers Using This Simple Bash Script
Conclusion
Finally, you are now familiar with the basics of networking. Reviewing the terminology beforehand will make your experience easier. Not to mention, it will give you the opportunity to maximize the potential of your server. This is because you are aware of the components and connections that permit communication within the system. Use this knowledge as a foundation to launch yourself into the world of networking operations.
Happy Computing!
- Removing Spaces in Python - March 24, 2023
- Is Kubernetes Right for Me? Choosing the Best Deployment Platform for your Business - March 10, 2023
- Cloud Provider of tomorrow - March 6, 2023
- SOLID: The First 5 Principles of Object-Oriented Design? - March 3, 2023
- Setting Up CSS and HTML for Your Website: A Tutorial - October 28, 2022


