What is SSH?
SSH means Secure Shell. With SSH you can access remote machines in a secure way since the connection is encrypted. With the ssh command from the Linux terminal, we can connect to remote Linux servers and work as if it were our computer. At the end of this tutorial, you should have a full understanding of how to use SSH to connect to a remote server in Ubuntu.
Syntax
The syntax is the rule of how you can use the ssh command. You can rearrange the syntax, but a direct format must be followed. Below is a syntax example for using the ssh command:
|
1 |
ssh remote_host |
The domain name or IP address you want to connect to is the remote_host as shown in the command above. This syntax assumes your username on the remote system and your local system are the same. However, in case the usernames are not the same, you can denote it with this command:
|
1 |
ssh remote_username@remote_host |
You will need to verify your identity by providing a password immediately when you connect to the server. Type the command exit to go back to your local session.
How To Configure SSH
The main sshd configuration file in Ubuntu is located at /etc/ssh/sshd_config. If you change the SSH configuration, the SSHD server settings will automatically change. Before any configuration, make sure you backup the current version of the file using this command:
|
1 |
sudo cp /etc/ssh/sshd_config{,.bak} |
Use a text editor to open it:
|
1 |
sudo nano /etc/ssh/sshd_config |
You should leave most of the parameters alone in this file. However, there are a few things that you should pay attention to:
|
1 |
Port 22 |
The port declarations indicate the port on which the SSHD server is waiting for connections. The default is 22. Unless there are specific reasons, you don’t need to change this setting:
|
1 2 3 |
HostKey /etc/ssh/ssh_host_rsa_key HostKey /etc/ssh/ssh_host_dsa_key HostKey /etc/ssh/ssh_host_ecdsa_key |
The host key declaration indicates where the global host key is located:
|
1 2 |
SyslogFacility AUTH LogLevel INFO |
The level of logs that should be done is indicated with these two items. If you have problems using SSH, an excellent way to identify the problem is to increase the number of logs:
|
1 2 3 |
LoginGraceTime 120 PermitRootLogin yes StrictModes yes |
These options define some information for the login to prevent unauthorized login when the configuration files are insecure:
|
1 2 |
X11Forwarding yes X11DisplayOffset 10 |
These parameter configurations are referred to as X11 forwarding functions. In this way, you can display the GUI of the remote system on the local system. You must enable this option on the server while connecting with the -X option to the SSH client.
After making changes, save the file and close it by pressing CTRL-X and Y and then press Enter. If you change settings in / etc / ssh / sshd_config, you must restart the sshd server to execute the change:
|
1 |
sudo service ssh restart |
For systemd systems such as Ubuntu 16.04 or Debian Jessie use this command:
|
1 |
sudo systemctl restart ssh |
Test your changes thoroughly to make sure that everything is working perfectly. You should probably keep some sessions active if you make any changes. In this way, you can restore the configuration if necessary.
How do you login to SSH with keys? It is good to log on to a remote system with a password. However, it is best to set up key-based authentication.
What is Key-based Authentication?
Key-based authentication creates two pairs of keys called a private and a public key. The private key is found on the user’s computer and has been protected and kept secret. The public key can be made available to anyone or stored on any server that you want to access. If you try to connect using a key pair, the server uses the public key to generate a message for the user computer. The user can only read the message using a private key. The user computer then sends a response back to the server and the server knows that the user is genuine. After setting the key, the entire process automatically completes in the background.
How To Create SSH Keys
SSH keys should be generated on the computer you wish to log in from. This is usually your local computer. Enter the following into the command line:
|
1 |
ssh-keygen -t rsa |
Then, accept the defaults by pressing the ENTER KEY. It will generate your keys at ~/.ssh/id_rsa.pub and ~/.ssh/id_rsa. Next, type the command below to change to the .ssh directory:
|
1 |
cd ~/.ssh |
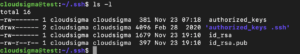
These are the files permission:
|
1 |
ls -l |
As you can see, only the owner can read and write the id_rsa file. Therefore, you must keep it safe. However, you can share the id_rsa.pub file and have the appropriate permissions for this activity. The next step is to transfer the public key to the server using this syntax:
|
1 |
ssh-copy-id remote_host |
This starts an SSH session and you must use a password for authentication. After entering the password, your public key will be copied to the server’s authorized key file so that you can log in the next time without a password.
How to Disable Password Authentication
If an SSH key is generated, you can improve the security of the server by disabling password-only authentication. You can log on to the server using the private key with the public key installed on the server instead of using the console.
Note: Make sure you installed the public key on the server before proceeding with this step. If not you will be blocked!
Open the sshd configuration file using this command:
|
1 |
sudo nano /etc/ssh/sshd_config |
Find and uncomment the line that reads password Authentication check by deleting the # at the beginning. Then you can change the value to “no”:
|
1 |
PasswordAuthentication no |
The PubkeyAuthentication and ChallengeResponseAuthentication are set by default and should look like this:
|
1 2 |
PubkeyAuthentication yes ChallengeResponseAuthentication no |
You should not change these two settings. After that, save the file and close it once you make the changes. Next, use the command below to restart the SSH daemon:
|
1 |
sudo systemctl restart ssh |
Finally, you have disabled the Password authentication, and your server can only be accessed using SSH key authentication.
Conclusion
In this tutorial, we have shown you how to use SSH to connect to a remote server securely in Ubuntu. Learning how to use SSH is fundamental if you are a system administrator, so after mastering this tutorial you can go on with more advanced functionalities of SSH.
Happy Computing!
- Removing Spaces in Python - March 24, 2023
- Is Kubernetes Right for Me? Choosing the Best Deployment Platform for your Business - March 10, 2023
- Cloud Provider of tomorrow - March 6, 2023
- SOLID: The First 5 Principles of Object-Oriented Design? - March 3, 2023
- Setting Up CSS and HTML for Your Website: A Tutorial - October 28, 2022